It has been 16 months since one of the largest cyber-attacks in the NHS’s history: on Friday, 12 May 2017, the first day of the attack, a total of 230,000 computers across 150 countries had already been infected with the ransomware WannaCry. Among the victims: FedEx, Deutsche Bahn, Télefonica; and parts of the NHS.
The worm wiggled its way into one of the most important IT systems in the UK by exploiting a known vulnerability of the Microsoft Windows operating system, encrypting files and displaying a ransom note. The note instructed the user to transfer a certain amount of the cryptocurrency bitcoin to an anonymous receiver, promising the decryption of files in return. The worm was also smart enough to identify vulnerable systems in the infected computer’s network, gain access to them and spread further.
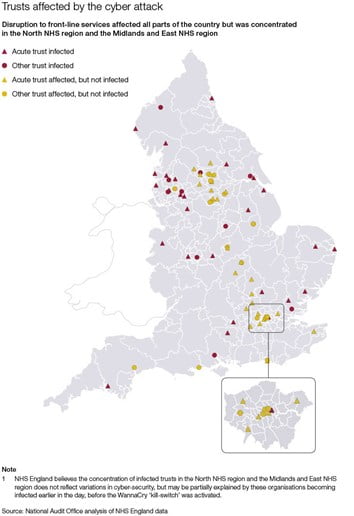
At least 85 Trusts were affected by the attack, as well as a further 603 primary care and other NHS organisations, including 595 GP practices. The impact was profound. An estimated 19,000 appointments were cancelled, including those of cancer patients; some Trusts were operating on emergency-only status; patient records, including X-rays and other essential data, became unavailable; phones stopped working; and pharmacies were instructed to disconnect from the NHS spine to avoid catching the infection that was taking over NHS IT systems, making prescriptions unavailable. There are no official numbers on how many ambulances were diverted and how many patients were turned away from the five A&E departments that had to stop treating less urgent cases.
Attacks like this significantly affect patient safety
With diagnostic tools such as X-rays becoming unavailable, it’s not only emergency medicine that is negatively affected. The impact on patients when urgent diagnostics and patient records become unavailable is dramatic. The same goes for delays in test results and prescriptions. There have been accounts of asthmatics who could not access their prescribed medication, and cancer patients having to wait for hours after receiving chemotherapy to take their prescriptions home because essential IT systems were unavailable. Likewise, patients requiring urgent lab results had to wait for days until they could be informed about the outcomes of their tests.
In the case of WannaCry, one essential element of the ransomware’s architecture was relatively unsophisticated (a poorly executed command-and-control function), and due to its timing, the attack was somewhat self-limiting. The impact on primary care was minimised merely by the fact that the attack began on a Friday and continued throughout the weekend when many practices are closed or have limited opening hours. The acute sector was not as lucky and continued to struggle throughout the 72 hours that the attack lasted. It came to an early end the following Monday when a security researcher from Devon accidentally discovered a kill switch in the worm’s code that stopped it from spreading further. However, despite its relatively contained nature, this attack brought home that IT is more than just an enabler of care. If things go wrong, attacks like this one have the potential to cause severe negative outcomes for patients, and potentially even casualties.
As an organisation committed to healthcare, people in the NHS understand better than anyone else the importance of prevention. The system works hard and committedly to intervene before people get sick. In the aftermath of the attack, severe shortcomings in the prevention of cyber-attacks became apparent. Despite warnings issued before about potential risks and existing vulnerabilities, the NHS did not respond in a sufficiently timely manner to patch known issues and prepare for a possible attack. This not only made it possible for the incident to happen despite it being preventable but also contributed towards the chaotic and unstructured response (NAO, 2017). Considering the severe impact and the potential patient harm that attacks like the WannaCry attack render, prevention and preparedness were shockingly low.
WannaCry happened. And it will happen again, in one way or another
WannaCry and its relatives are still out there. And much like their biological namesakes, computer viruses and worms learn and adapt: there are samples of WannaCry and other ransom and malware out there that do not have a kill switch. The NHS and affiliated organisations need to understand that attacks like the one in May 2017 pose a direct threat to the lives of the people they care for. Safe, protected, maintained and up to date IT systems are not a luxury – they play a crucial part in keeping people alive and should be treated with the appropriate care. Hackers and criminals are not getting slower – the NHS has to get quicker if it wants to avoid another 12 May.
Each organisation is responsible for ensuring their systems are as safe as they can be. NHS England, NHS Improvement, and the Department of Health and Social Care published a ‘lessons learned’ paper approximately one year after the attack.
What can we learn from WannaCry?
Update, patch, repeat
One of the most avoidable causes was the lack of sufficient patching. ‘Patch Tuesday’, Microsoft’s monthly patch and update release day need to become a recurrent fixed date in NHS calendars. Criminals reverse-engineer patches to develop targeted exploits, often in as little as 24 hours: for this reason, the term ‘Exploit Wednesday’ has been coined. The NHS, therefore, needs to set up highly efficient processes to allow same-day patching.
Prepare, and don’t panic
The NHS has demonstrated structure, organisational excellence, and bravery in the face of adverse events. The same level of whole organisation preparedness needs to be achieved for IT security incidents. NHS England recommends annual cyber awareness training and suggests that “all organisations should consider whether access to IT systems and services should be removed from members of staff who have not successfully completed this mandatory training.” Staff should be trained on how they should react if their organisation is the target of an attack, how they contribute to containing the spread of the malware, and how they can minimise local impact.
Digital quarantine
NHS England also recommends the development of a centralised system that would allow NHS Digital to “have the ability to isolate organisations, parts of the country or particular services in order to contain the spread of a virus during an incident”. This would mean a significant infrastructural project, which is likely to take a number of years. In the 2017 WannaCry attack, the NHS was not the primary target, but rather collateral damage in what was a global incident. One can only imagine the potential damage if the NHS was targeted directly in a similar manner. To reduce risk and improve resilience, it is critical that any improvements ‘digital infection control’ is made a priority.




